Understanding and Spoofing Computer Information with EyeDown

In the digital world, maintaining privacy and anonymity often requires more than just using incognito modes or VPNs. A crucial yet often overlooked aspect is the information embedded in your computer’s hardware and system configurations. These details can be exploited to track and identify your device uniquely. EyeDown offers a comprehensive solution to spoof these identifiers, significantly enhancing your privacy and security. Let’s delve into what these information types are, their importance, and how EyeDown helps in spoofing them.

Key Computer Information and Their Uses
Here is a comprehensive list of the computer information you can spoof with EyeDown and the benefits associated with each. To spoof, just check the box next to the information you want to spoof and click on “Spoof selected information.” The intuitive design makes it easy for anyone to enhance their privacy and security with just a few clicks.
MAC Address
- Use: Each network interface card (NIC) in your device has a unique Media Access Control (MAC) address, which is used to identify devices on a network.
- Spoofing Benefit: Changing the MAC address helps in preventing network-based tracking and enhances privacy on public and private networks.
Computer’s Public Name
- Use: This is the name your computer broadcasts on networks, often revealing user or device identity.
- Spoofing Benefit: Modifying this name prevents unique identification on local and public networks, maintaining anonymity.
OEM Manufacturer Name
- Use: The name of the original equipment manufacturer (OEM) stored in the system information.
- Spoofing Benefit: Changing the OEM name hides the true identity of the manufacturer, preventing profiling based on hardware origin.
OEM Computer Model
- Use: The model name of your computer as specified by the manufacturer.
- Spoofing Benefit: Altering the computer model name helps in obscuring the actual model, adding a layer of privacy.
OEM Manufacturer Number
- Use: This number uniquely identifies the manufacturer of the device.
- Spoofing Benefit: Changing this number prevents tracking based on manufacturer identification.
Product Name
- Use: The specific product name or version of your device.
- Spoofing Benefit: Modifying the product name conceals the true identity of your computer.
Motherboard Manufacturer
- Use: The name of the motherboard manufacturer.
- Spoofing Benefit: Changing the manufacturer name of the motherboard helps in preventing hardware-based tracking.
Motherboard’s Active Label
- Use: Identification label for the motherboard.
- Spoofing Benefit: Modifying this label hides the motherboard’s identification details.
BIOS Version
- Use: The version number of your BIOS, which provides system firmware.
- Spoofing Benefit: Changing the displayed BIOS version hides the actual firmware version, making tracking more difficult.
BIOS Release Date
- Use: The release date of your BIOS firmware.
- Spoofing Benefit: Modifying this date helps in obscuring information about the system firmware version.
Manufacturing Plant
- Use: The location where your device was manufactured.
- Spoofing Benefit: Changing this information hides the origin of your computer, preventing geographical profiling.
System Version
- Use: The version of the operating system installed on your device.
- Spoofing Benefit: Modifying the system version displayed helps in concealing the true OS version.
System Family Name
- Use: The family or series name of the operating system.
- Spoofing Benefit: Changing the system family name adds an extra layer of privacy.
Motherboard Manufacturing Plant
- Use: The location where the motherboard was manufactured.
- Spoofing Benefit: Modifying this information hides the origin of the motherboard.
Card Product Name
- Use: The name of the product for the motherboard or graphics card.
- Spoofing Benefit: Changing this name helps in obscuring the identity of key hardware components.
Motherboard Version
- Use: The version of the motherboard installed in your system.
- Spoofing Benefit: Modifying the displayed motherboard version hides the actual hardware details.
Motherboard Chassis Position
- Use: Information about the position of the motherboard in the chassis.
- Spoofing Benefit: Changing this information prevents identification based on installation details.
Chassis Manufacturing Plant Name
- Use: The name of the plant where the chassis was manufactured.
- Spoofing Benefit: Modifying this name hides the origin of the computer case.
Chassis Type Name
- Use: The type or model name of the chassis.
- Spoofing Benefit: Changing this type name helps in concealing the identity of the computer case.
Chassis Version
- Use: The version number of the chassis.
- Spoofing Benefit: Modifying this version hides the actual version information.
Power Cord Information
- Use: Details about the power cords used in the computer.
- Spoofing Benefit: Changing this information prevents tracking based on power component details.
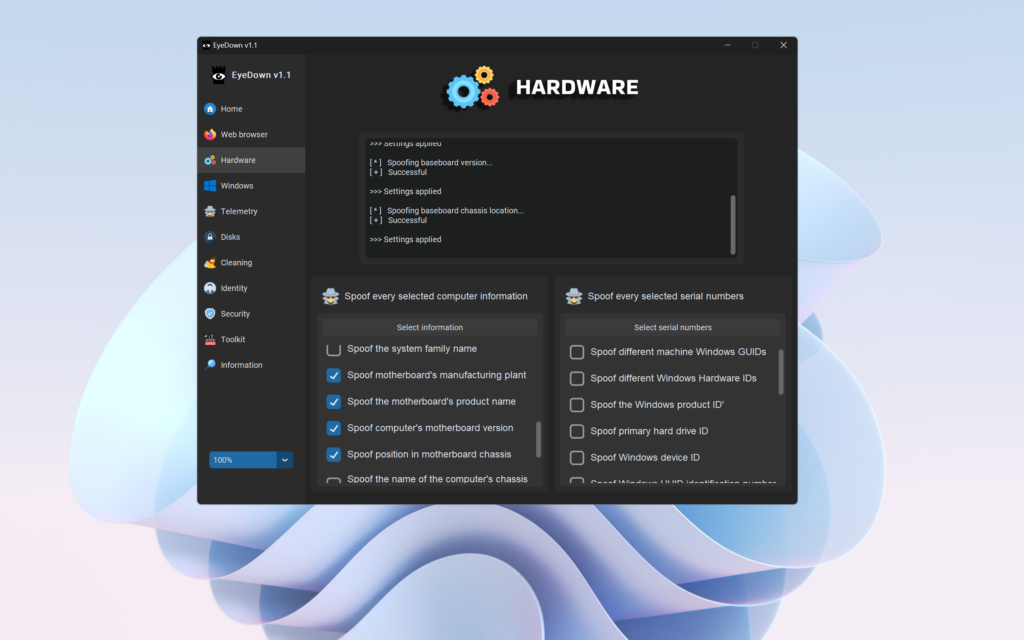
Why Use EyeDown for Spoofing?
EyeDown excels in providing a user-friendly and comprehensive solution for spoofing these critical computer information types:
Ease of Use: EyeDown’s intuitive interface makes it easy for users to spoof various hardware details without needing extensive technical knowledge.
Comprehensive Coverage: EyeDown covers a wide range of hardware identifiers, ensuring all potential tracking vectors are addressed.
Regular Updates: EyeDown is regularly updated to stay ahead of new tracking methods and ensure continuous protection.
Enhanced Privacy Tools: Beyond spoofing, EyeDown integrates additional privacy tools such as script blockers, ad blockers, and tracking prevention, offering a holistic approach to online anonymity.
Conclusion
Spoofing your computer’s information is a crucial step in maintaining online privacy and preventing tracking. EyeDown stands out as the best tool for this task, providing comprehensive spoofing capabilities and an easy-to-use interface. By using EyeDown to spoof your computer’s information, you can significantly enhance your online privacy and protect yourself from tracking and profiling.
Experience unparalleled privacy protection with EyeDown and take control of your digital footprint today.